Leading Global Brands Trust ArangoDB


ML Powered Insights from Connected Data
Explore The ArangoDB Difference
Watch these 2-3 minute videos to understand ArangoDB’s Differentiation
Model Flexibility
DB Consolidation
Vs. Legacy Graph
Any Cloud. Any Architecture.
Run on Any Cloud
Choose your favored cloud platform with ArangoGraph, a full-managed, scalable, and high-performance graph database service that delivers the added value of an integrated document store, full-text search engine, and geospatial capabilities. This unified solution offers seamless, hassle-free management of these diverse data models and types, relieving you of operational overhead and allowing you to focus on innovation and development.
Advanced
Deployment Options
Run on ANY system. Plus, ArangoDB supports Kubernetes through its official Kubernetes Operator, which allows users to deploy and manage ArangoDB clusters within a Kubernetes environment. And with Docker, you can easily deploy and run ArangoDB containers on various platforms, including local development environments, cloud infrastructure, and Kubernetes clusters.

Any Cloud. Any Architecture.
Develop With Your Favorites
Choose the widest range of clients of any graph database, giving you the flexibility to deploy applications fast and with languages you know and support. Developers leverage their existing knowledge base and experience, thereby reducing the learning curve and enabling more efficient and effective creation and implementation of solutions.

One Language
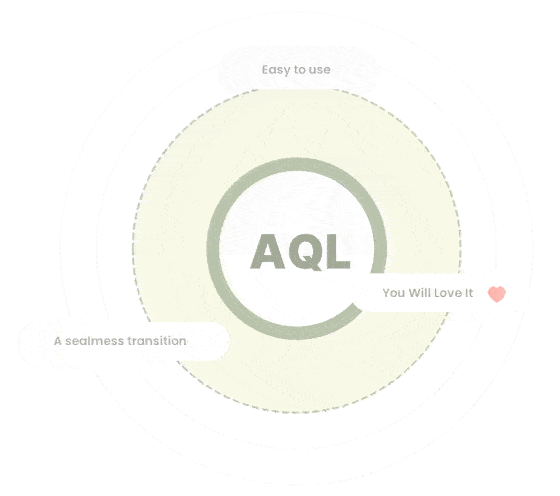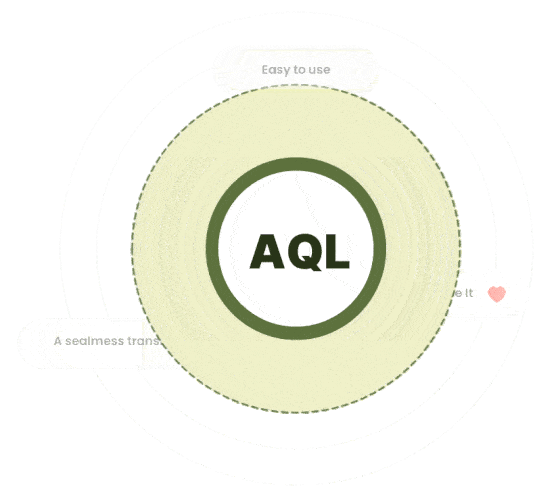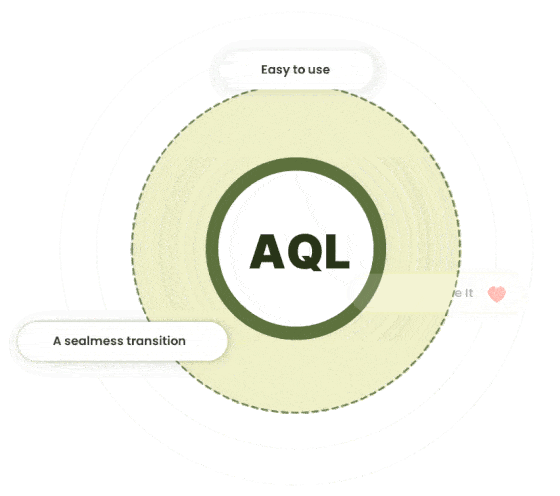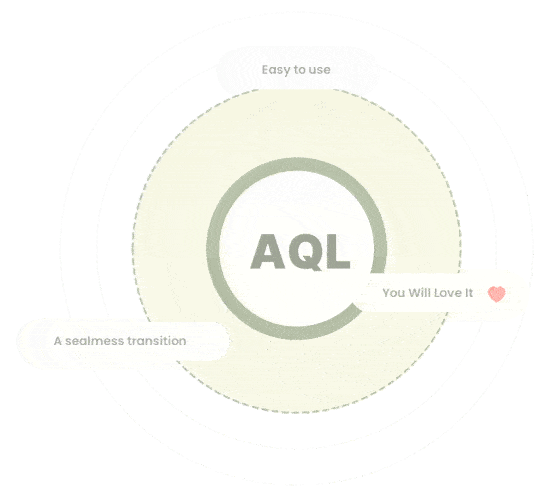
One Query Language To Rule Them All
AQL is a unified query language letting you access all your data with a broad range of access patterns like traversals, JOINs, search, geospatial or any combination. Everyone experienced with SQL will have an easy start with AQL and might think AQL feels more like coding.
Confidence
Deploy with Confidence
Fully-Managed SaaS Graph DB
ArangoGraph, built on the ArangoDB Graph Database.
“With ArangoGraph, we've consolidated all the services of search, graph and document data stores and that advances us leaps and bounds. Using ArangoGraph was the obvious choice”
- Anna Spyker
Lead Data Engineer
Decoded Health
On Prem / Self-Managed Graph DB
Graph, integrated search engine, JSON support, and Key/Value via a single query language.
“ArangoDB Enterprise was the only Graph DB that featured a document model as well as graph. With Neo4j, well, it has a nice language if you want, but you have a lot of limitations and you don't have documents.”
- Vasilis Tsolis
Founder & CEO
Cognitiv+